Kerberos: Setting up a Kerberos Server

| Software version | 5 |
| Operating System | Red Hat 6 Debian 6 |
Introduction
Kerberos is a network authentication protocol that relies on a secret key mechanism (symmetric encryption) and the use of tickets, rather than clear text passwords, thus avoiding the risk of fraudulent interception of user passwords. Created at the Massachusetts Institute of Technology (MIT), it bears the Greek name for Cerberus, guardian of the Underworld. Kerberos was first implemented on Unix systems.
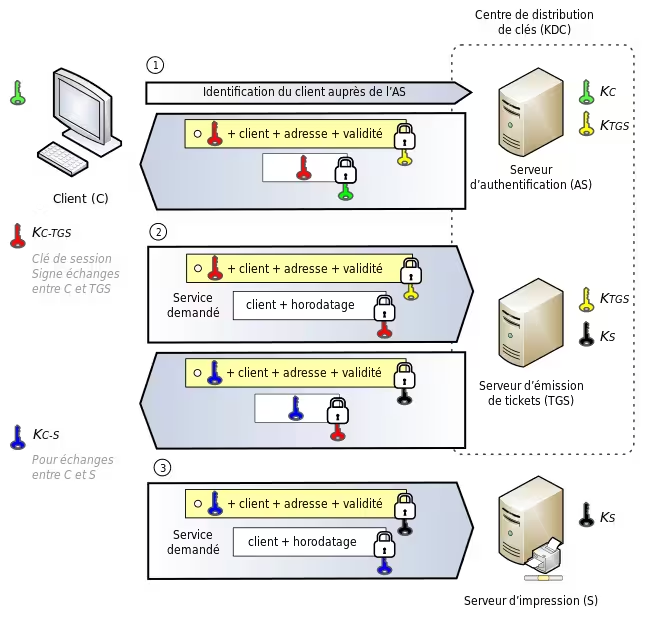
In a simple network using Kerberos, several entities are distinguished:
- The client (C) has its own secret key Kc
- The server (S) also has a secret key Ks
- The ticket-granting service (TGS) has a secret key KTGS and knows the secret key KS of the server
- The key distribution center (KDC) knows the secret keys KC and KTGS
Client C wants to access a service offered by server S.
We will first see how to set up a Kerberos server under GNU/Linux. Then in the second part, we will look at client configuration and system authentication via PAM.
Server Installation
To install Kerberos:
Server Configuration
The krb5.conf file will need to be configured on all clients. It indicates the different realms and their respective KDC (Key Distribution Center = Kerberos server). Edit /etc/krb5.conf and adapt to your configuration:
The kdc.conf file contains the Kerberos server configuration:
Creating the Kerberos Database
The creation of the Kerberos database is done via the following command (the -s option allows storage in a file):
The password requested here will be used to encrypt the database. From now on, we can verify access to the KDC via the kadmin.local command. This is identical to the kadmin command but bypasses the root ACLs (local use only).
Creating Accounts
We can already check the main accounts created by default:
User creation is done via the ank command: Add New key
The key must then be stored in a special file called keytab:
The file /etc/krb5kdc/kadm5.keytab should now contain the corresponding keys.
Finally, set up ACLs to give all privileges to accounts with an admin instance. Edit /etc/krb5kdc/kadm5.acl:
Server Launch
Start the server as follows:
Client Installation
Client Configuration
Copy the /etc/krb5.conf file from the server.
Tests
To test that everything works correctly, you should be able to perform the following sequence:
Obtaining a ticket for the admin principal:
Display of current tickets:
Destroying the ticket:
Setting up System Authentication
PAM Configuration
On the client, we will use PAM. To do this, add the following lines to the different files. Edit the file /etc/pam.d/common-auth:
Edit /etc/pam.d/common-account:
Edit /etc/pam.d/common-password:
Edit /etc/pam.d/common-session:
Adding a User
On the server, create a user named olivier:
Now we can do:
Let's now create the user olivier on the client:
Edit the /etc/shadow file:
The encrypted password here, K, is used to indicate that the password comes from Kerberos.
Test
From a third machine, SSH to the Kerberos client:
By doing a tail -f /var/log/auth.log on the server, you should get: