Grimwepa: Easy WiFi Hacking
Introduction
This method is really designed for beginners and allows for easy cracking of wireless networks without any networking knowledge. It's not the kind of method I usually prefer since it enables 16-year-olds to think they're NASA-level hackers with these tools... but anyway.
This method is very practical when you don't have much time. For the OS, I obviously recommend BackTrack, but Ubuntu can also work. For this tutorial, I'll use Ubuntu.
Installation
aircrack-ng
Let's install aircrack-ng to get all the necessary binaries:
Grimwepa
It's recommended to install grimwepa using this method:
Configuration
For configuration, we just need to activate monitoring mode on our wireless interface. I'm using a DLINK DWL-G122 with a RALINK chipset that allows me to perform injections, etc. To activate this mode:
Monitor mode is now active on mon0 :-)
Utilization
Now, let's launch grimwepa:
Select the mon0 interface, then click on "Refresh Targets", you should see it scanning:
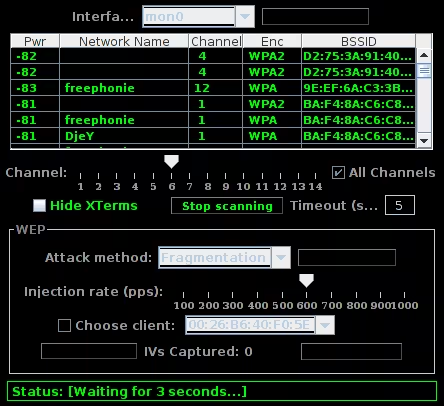
Stop after about 3 scans, that's sufficient. Choose a network with WEP encryption (faster because it's older and therefore easier to crack). Then select "Fragmentation" as the attack method and choose an available client. Then click on "Start Attack":
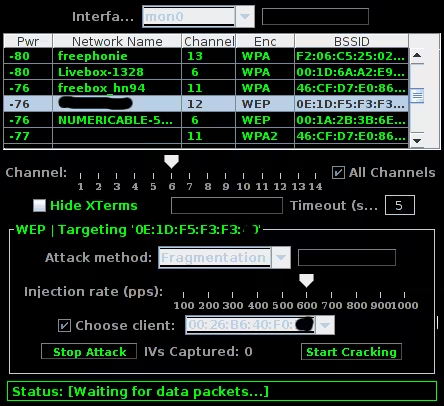
A window should open that will listen to what's happening on this network:
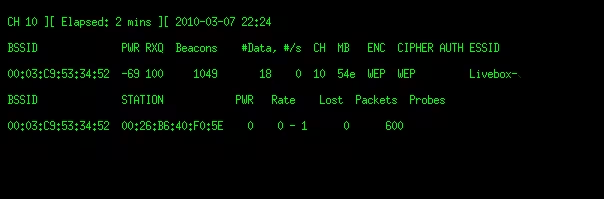
Once there is enough data (which can take some time depending on traffic), an airmon-ng window will start to launch injections. From this point, it will go relatively quickly. The WEP key cracking will follow. The key will then be displayed in the status.